Guessing Login passwords with Hydra
This post will help us learn how to create our own dictionary of passwords and then launch attacks on login forms using the dictionary we created along with the Kali based tool Hydra. These days almost all the websites contain authentication forms. Therefore, this tool is very handy when launching brute-force attacks. So, before getting our hands dirty with the tool; let us first polish some of our basics about dictionary and brute-force attacks.
Brute-force attack vs Dictionary Attack
We often use brute-force and dictionary attack interchangeably and it is somewhat right but there is a subtle difference between them. We can think brute-force attack as a superset of dictionary attack. Brute-force attacks are exhaustive attacks which tries all the possibilities (viz. letters, characters, special characters, and their combinations as well) where as in dictionary attack we provide a dictionary i.e. list of words(can be letters, characters and also their combinations) from which the target system is penetrated with. Brute-force attacks being exhaustive will ensure that you’ll get the field data(password filed, username, etc.), but as it is exhaustive; the time taken will vary(will be enormous for secured passwords). On the other hand, dictionary attacks are selective so, it may provide false positives but it is fast. So, practically we prefer dictionary attacks rather than brute-force.
Creating our own dictionary with crunch
So before we begin launching attack with hydra, we must be ready with our dictionary of passwords which we are going to use. Although we can use the dictionaries which are already present on the internet(my favorite repo); but in case you want to be more specific with the target you might require to create your own. There is a very handy tool called crunch which helps in doing this task for us.
You can generate the dictionary that fits your needs. So, Let us generate a dictionary which contains password with length 8 and has letters abcd and numbers 1234.
~# crunch 8 8 abcd1234 -o /Desktop/dict.txt -t a@@@@@@4
Crunch will now generate the following amount of data: 2359296 bytes
2 MB
0 GB
0 TB
0 PB
Crunch will now generate the following number of lines: 262144
crunch: 100% completed generating output
Command overview:
- crunch - name of the tool
- 8 - minimum length
- 8 - maximum length(Since I want to create smaller wordlist so I took both the lengths same)
- -o - Location where the dictionary gets created
- -t - Pattern if any of the passwords(In the above case all the passwords in the dictionary should start with a and end in 4)
There are however numerous options of creating wordlists using crunch. You can explore all the options to get the better insight. I presume you already know how to man any tool in linux ![]() [man crunch].
[man crunch].
Guessing Login password Using a wordlist attack with Hydra:
Now, that our dictionary is ready next thing to do is to launch the wordlist attack. The tool which we are going to use is Hydra(as evident in the blog title obviously![]() ). Hydra is a very simple tool to use but in the contrary very powerful and efficient in launching brute-force and dictionary attacks on almost any authentication services(like routers, web applications, etc.) which I can think of.
). Hydra is a very simple tool to use but in the contrary very powerful and efficient in launching brute-force and dictionary attacks on almost any authentication services(like routers, web applications, etc.) which I can think of.
Using the tool is simple. Fire up the terminal and type the command below:
hydra [IP] -L[usernames] -P[password list] [service]
Command overview:
- hydra - Name of the tool
-
IP - IP address of the target website (I presume you can convert the domain names to ip addresses
 [dig +short www.example.com])
[dig +short www.example.com]) - -L - List of usernames to brute-force the target. Use -l for giving just one user.
- -P - List of passwords to brute-force the target. Use -p for providing one password.
- service - Providing the type of service you are attacking. This is the most tricky part of the command but is very simple once you get the understanding.
Let us see it in action using an example. I am using metasploitable machine to demonstrate this example. The application name is dvwa.
- We have to launch the attack on dvwa web application as shown below:
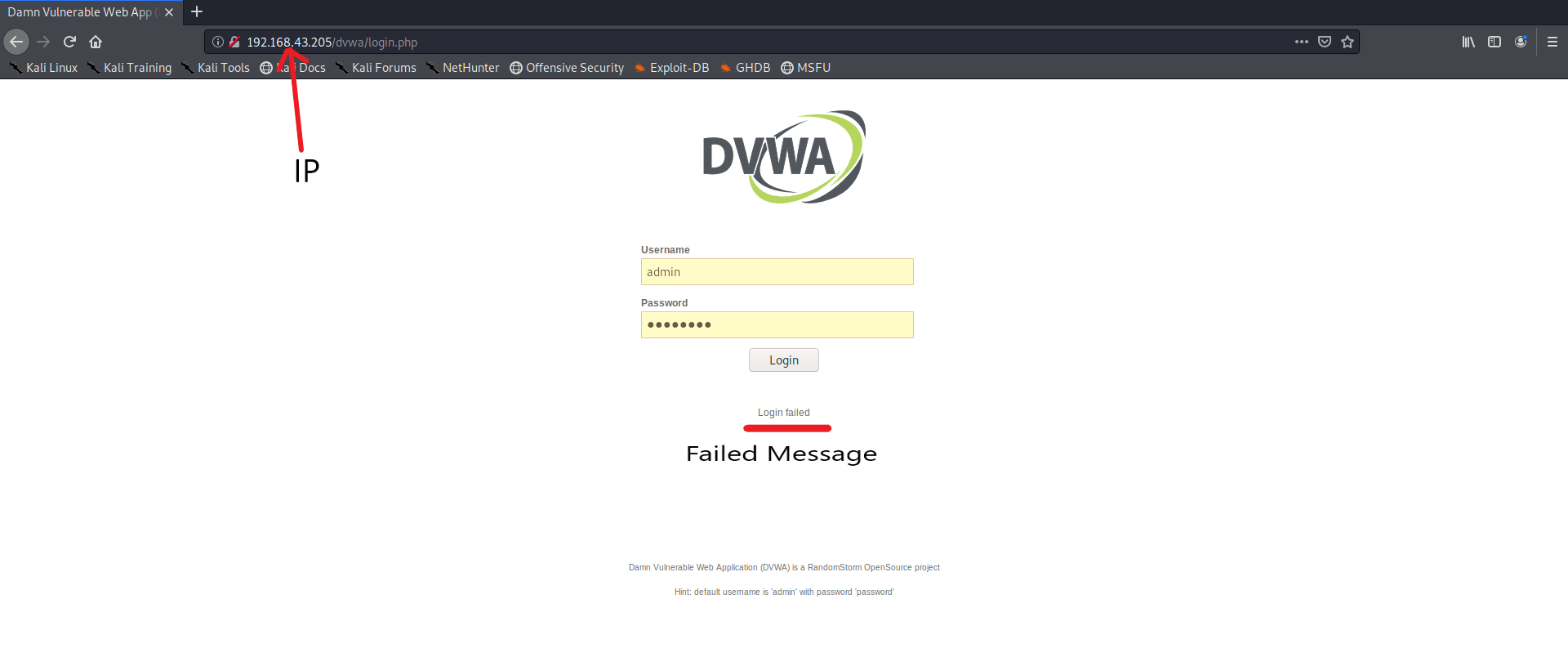
-
From the page we have got our IP address, the protocol on which it is running(http) and Failure login Message(Don’t worry!I’ll let you know where the former two parts will be useful).
-
Now the next thing, which we need to do is to inspect the action type of the form which this web application is using(I presume you know how to get the form action type
 [Right click on the form and click on inspect element]).By doing this; we came to know about the form type i.e. POST. If you’ll know the difference between GET and POST, you’ll know that POST requests are hidden. They are not visible in the url.
[Right click on the form and click on inspect element]).By doing this; we came to know about the form type i.e. POST. If you’ll know the difference between GET and POST, you’ll know that POST requests are hidden. They are not visible in the url. -
Next thing which we need is to do is to find out what are the parameters which are sent to the server along with username and password. To know this, we are going to use BurpSuite; another very helpful tool for hackers. I’ll talk about it in some other blog later. For quick gist, I’m using BurpSuite’s proxy to intercept HTTP requests. Below is the image which shows the parameters that are sent to dvwa server when I used username as admin and password as somerandompass.
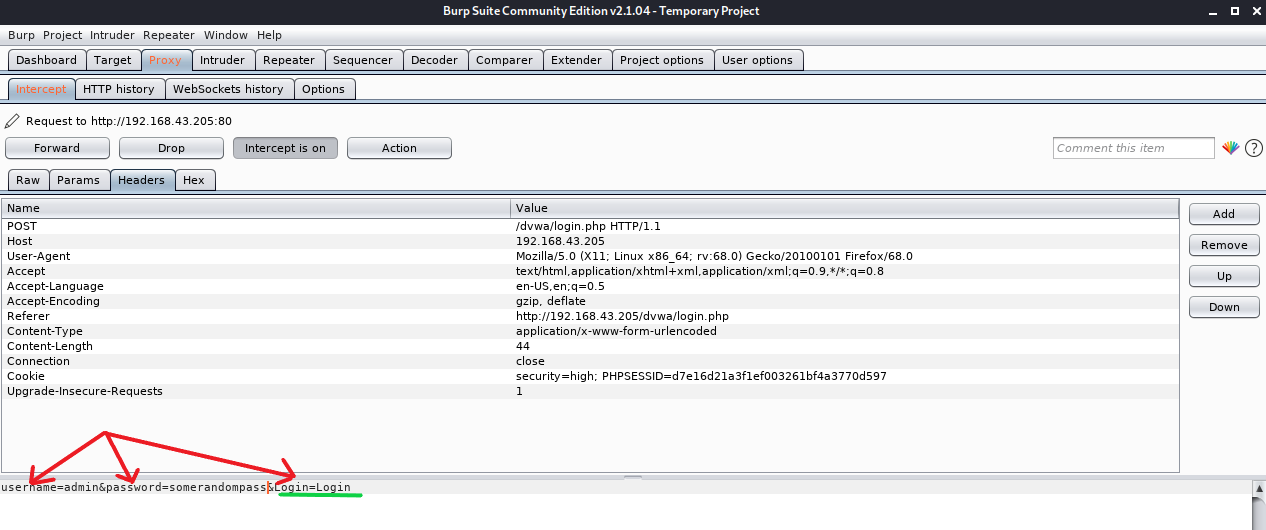
- That’s it; we have all the things needed to construct our command for hydra. Now, let us write the full command and understand its service type part in detail.
hydra 192.168.43.205 -l admin -P dict.txt http-post-form “/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:F=Login failed”
Command Overview[The service Part]:
- http-post-form - It is the name of the service which tells hydra what the web app is using. You can man it to get more info.
-
“/dvwa/login.php:username=^USER^&password=^PASS^&login=Login:F=Login Failed” - This part which is enclosed in quotes contain three colons. Let us break them down one by one.
- Ist part: This part of the colon represents the page where the attack needs to be launched.
- IInd part: This part of the colon represents the parameters that are passed to dvwa server every time the user tries to log in(The reason why we used Burp proxy).
- IIIrd part: This part of the colon shows what is the text that will be visible on the page when login failure(because we used F option) occurs.
Finally, fire up the terminal and paste the above command, and you’ll see the result below:
~# hydra 192.168.43.205 -l admin -P dict.txt http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:F=Login failed"
Hydra v9.0 (c) 2019 by van Hauser/THC - Please do not use in military or secret service organizations, or for illegal purposes.
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2020-04-21 16:14:47
[DATA] max 16 tasks per 1 server, overall 16 tasks, 262146 login tries (l:1/p:262146), ~16385 tries per task
[DATA] attacking http-post-form://192.168.43.205:80/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:F=Login failed
[STATUS] 504.00 tries/min, 504 tries in 00:01h, 261642 to do in 08:40h, 16 active
[80][http-post-form] host: 192.168.43.205 login: admin password: a11bdd44
1 of 1 target successfully completed, 1 valid password found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2020-04-21 16:16:02
Bingo![]() , we found the password for the username admin i.e. a11bdd44.
, we found the password for the username admin i.e. a11bdd44.
Give these tools a try and explore various other features and options available for these tools. Keep hacking for good and keep growing always.